SANS.edu Research Journal Volume 3 Released into the Wild. https://www.sans.edu/cyber-security-research @sans_edu #cybersecurity #research, (Sun, Apr 30th)
Updated: 2023-04-30 20:33:42
---
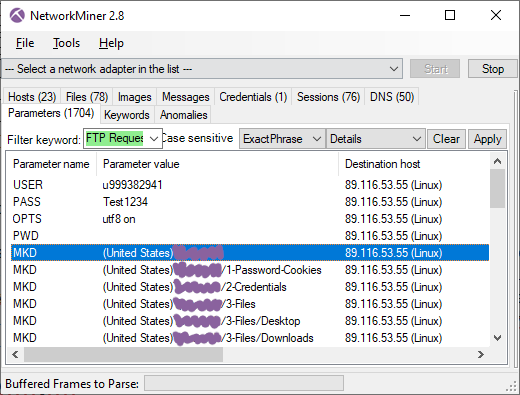 I analyzed a PCAP file from a sandbox execution of the Evil Extractor stealer malware earlier today. This stealer collects credentials and files of interest from the victim's computer and exfiltrates them to an FTP server. It is designed to autonomously collect and exfiltrate data rather than receiv[...]
I analyzed a PCAP file from a sandbox execution of the Evil Extractor stealer malware earlier today. This stealer collects credentials and files of interest from the victim's computer and exfiltrates them to an FTP server. It is designed to autonomously collect and exfiltrate data rather than receiv[...]